Table Of Content
- Public Protection Notification
- II. Analysis of Public Comments and Consideration of the 12 Factors of the EPAct
- List of Subjects in 10 CFR Part 73
- XVI. Backfit Analysis
- Resource Materials
- III. Summary of Specific Changes Made to the Proposed Rule as a Result of Public Comment
- Group I: Consideration of the 12 Factors in the Energy Policy Act
Establishing such a DBT can provide a valuable planning tool for the Transmission Operators and their partners who are responsible for blackstart operations. In particular, as cyber and other threats to blackstart assets and capabilities continue to intensify, DBTs can help system owners and operators target their investments to maintain system resilience. A formal DBT also can provide regulators confidence that those investments are prudent, and deal with ongoing challenges in the availability of gas-fueled cranking-path generators. One significant change to the rule relates to physical threats from the use of vehicles, either as modes of transportation or as vehicle bombs. Section 73.1(a)(1)(i)(E), for example, effectively expands the scope of vehicles available for the transportation of adversaries by deleting the reference to “four-wheel drive” and by adding water-based vehicles. The competent authorities should regularly review the national threat assessment and the DBTs and revise them as needed.
Public Protection Notification
Each plant was requested to consider implementation of applicable additional strategies by August 31, 2005. The NRC inspected each plant in 2005 to review their implementation of any additional mitigative measures. In addition, § 73.1(a)(1)(iii) (the land vehicle bomb provision) is similarly revised to delete the “four-wheel drive” limitation, and to add a capability that the vehicle bomb “may be coordinated with an external assault,” maximizing its destructive potential. Further, an entirely new capability has been added to the DBT involving a waterborne vehicle bomb, which also is encompassed in the coordinated attack concept. This ISC Standard defines the criteria and processes facility security professionals should use in determining a facility's security level. This standard provides an integrated, single source of physical security countermeasures and guidance on countermeasure customization for all nonmilitary federal facilities.
II. Analysis of Public Comments and Consideration of the 12 Factors of the EPAct
The Commission expects that licensees and State and Federal authorities will use whatever resources are necessary in response to both DBT and beyond-DBT events. The NRC also initiated a program in 2002 to assess the capability of nuclear facilities to withstand a terrorist attack. As the results of that program became available, the NRC provided power reactor licensees additional guidance in February 2005 on the implementation of the February 2002 Order regarding spent fuel mitigation measures. Mitigating measures that are being or have been established include those specifically recommended in the NAS study regarding fuel distribution and enhanced cooling capabilities. Though the following topics and comments are pertinent to the security issues of nuclear facilities, they are not directly relevant to the DBT rulemaking. The DBT rule identifies general threat characteristics, but does not require specific protective strategies and security measures to defend against and thwart attacks.
List of Subjects in 10 CFR Part 73
A reasonable approach in determining the threat requires making certain assumptions about these shared responsibilities. Although licensees are not required to develop protective strategies to defend against beyond-DBT events, it should not be concluded that licensees can provide no defense against those threats. The NRC has authorized the Duke Energy Corporation, owner and operator of the Catawba plant, to irradiate four fuel assemblies of Mixed-Oxide (MOX) fuel at the Catawba plant on a test basis as part of its license amendment issued on March 3, 2005. MOX fuel technically meets the criteria of a formula quantity of Strategic Special Nuclear Material, in this case plutonium, and would be subject to the DBT provisions of § 73.1(a)(2) for theft or diversion. However, the NRC staff found that MOX fuel is not attractive to potential adversaries from a theft and diversion standpoint at the reactor site due to its low plutonium concentration, composition, and form (size and weight). The MOX fuel consists of plutonium oxide particles dispersed in a ceramic matrix of depleted uranium oxide with a plutonium concentration of less than six weight percent.
The large aircraft impact studies included structural analyses of the aircraft impact into a single cask and the resulting cask-to-cask interactions. Those evaluations indicate that it is highly unlikely that a significant release of radioactivity would occur from an aircraft impact on a dry spent fuel storage cask. Dry cask storage facilities (e.g., independent spent fuel storage installations (ISFSIs)) at nuclear power plants are designed to protect against external events such as tornados, hurricanes, fires, floods, and earthquakes. The standards in 10 CFR Part 72 Subpart E, “Siting Evaluation Factors,” and Subpart F, “General Design Criteria,” ensure that the dry cask storage designs are very rugged and robust. The casks must maintain structural, thermal, shielding, criticality, and confinement integrity during a variety of postulated external events including cask drops, tip-over, and wind driven missile impacts. After the September 11, 2001 attacks, the NRC has worked with licensees, the DHS, and State and local governments to improve the capabilities of first responders as part of the National Infrastructure Protection Plan.
Resource Materials
Licensees were subsequently provided with a cyber security self-assessment methodology and the results of pilot studies, as well as additional guidance issued by the nuclear industry, to facilitate development of site cyber security programs. After the terrorist attacks of September 11, 2001, the Commission initiated a program in 2002 to assess the capability of nuclear facilities to withstand terrorist attacks. As part of the program, the Commission analyzed the performance of ISFSIs under aircraft attacks and has evaluated the results of detailed security assessments involving large commercial aircraft attacks, which were performed on four representative spent fuel casks.
Colonial touts cyber 'best practices.' It was still hacked - E&E News by POLITICO
Colonial touts cyber 'best practices.' It was still hacked.
Posted: Wed, 19 May 2021 07:00:00 GMT [source]
Webinar on Safety, Security and Safeguards Interfaces and Challenges for Novel Advanced Reactors IAEA - International Atomic Energy Agency
Webinar on Safety, Security and Safeguards Interfaces and Challenges for Novel Advanced Reactors IAEA.
Posted: Thu, 03 Feb 2022 08:00:00 GMT [source]
NNSA’s safeguards and security program has multiple areas of deterrence including protective force, physical security, information security, material control and accountability, personnel security, and security program operations and planning. These programs integrate personnel, equipment, and procedures to protect physical assets and resources against theft, sabotage, diversion, and other criminal acts. The national nuclear security threat assessment result is used to develop material-, facility- or activity-specific DBTs. Plants licensed to operate before January 1, 1979, must comply with fire protection requirements as specified in 10 CFR 50.48(b) that backfit paragraphs III.G, J and O of Appendix R. Plants licensed to operate after January 1, 1979, must comply with the approved fire protection program incorporated into their operating license. When the Commission promulgated 10 CFR Part 50, Appendix R, the Commission recognized that there would be plant specific conditions and configurations where strict compliance with the prescriptive features specified in Appendix R would not significantly enhance the level of fire safety already provided by the licensee. Other commenters charged that the DBT rulemaking is simply codifying secret orders to avoid public scrutiny.
Design Basis Threat Development is Key to Proper “Blackstart” Grid Capability

PRM–73–12 requests that the NRC amend its regulations to revise the DBT regulations (in terms of the numbers, teams, capabilities, planning, willingness to die, and other characteristics of adversaries) to a level that encompasses, with a sufficient margin of safety, the terrorist capabilities evidenced by the attacks of September 11, 2001. The NRC partially granted PRM–73–12 in the proposed rule, but deferred action on other aspects of the petition to the final rulemaking. The Commission is confident that a licensee's security force would respond to any threat no matter the size or capabilities that may present itself.
Group I: Consideration of the 12 Factors in the Energy Policy Act
This final rule does not contain new or amended information collection requirements and, therefore is not subject to the Paperwork Reduction Act of 1995 (44 U.S.C. 3501 et seq.). Existing information collection requirements were approved by the Office of Management and Budget, approval number 3150–0002. The burden for all future licensees will be covered under 10 CFR Part 52 (3150–0151) as part of the combined operator license applications. (B) Items that could facilitate theft of special nuclear material (e.g., small tools, substitute material, false documents, etc.), or both. Industry commenters suggested that the ACDs and RGs should be incorporated by reference into the DBT rule to ensure adequate stakeholder participation in changes to the specific details of the DBTs. Otherwise, these commenters argue that the use of the ACDs and RGs has the potential for circumventing the APA and Paperwork Reduction Act.
The NRC will consider using a voluntary consensus standard if an appropriate standard is identified. Design Basis Threats (DBT) and Representative Threat Statements (RTS) are two of the most prominent tools proposed by the updated IAEA guidance. To request access, email with your full name and contact information, including email, agency name, and reason for access.
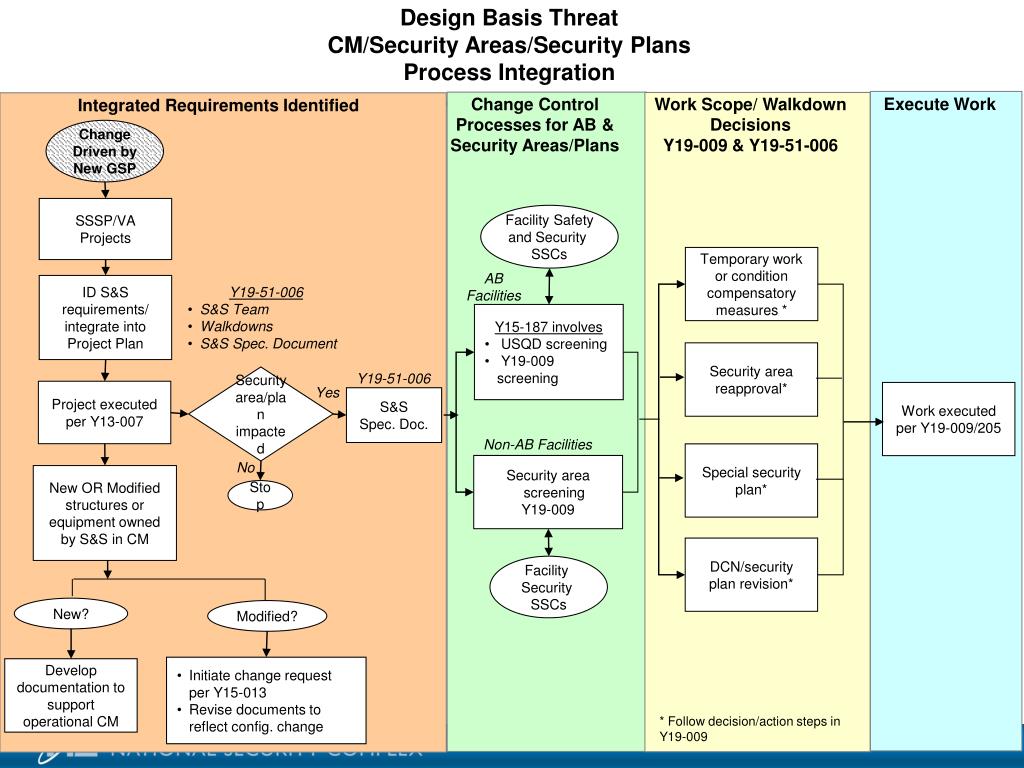
[4] Requirement R4 of CIP provides that the evaluation of potential threats and vulnerabilities should be based on the “unique characteristics” of the transmission substation or control center, prior history of attacks on similar facilities and intelligence information. Requirement R6 provides that those evaluations are subject to verification by an independent qualified third-parties. Today’s range and sophistication of threats to the grid, and the certainty that more will emerge, strongly suggests that having DOE-developed DBTs, whether they are turned into NERC Reliability Standards or codified through another mechanism, will provide needed certainty on requirements needed for blackstart. And proposed solutions that consider all known and likely threats will provide a more efficient outcome.
The NRC has taken numerous actions to enhance the security of spent nuclear fuel, and will take appropriate additional action as necessary as a result of on-going evaluations. Before September 11, 2001, spent fuel was well protected by physical barriers, armed guards, intrusion detection systems, area surveillance systems, access controls, and access authorization requirements for employees working inside the plants. After September 11, 2001, the NRC has enhanced its requirements, and licensees have increased their resources to improve security at nuclear power plants. For example, the NRC's February 25, 2002 Order to power reactor licensees dealt with spent fuel pool cooling capabilities in the event of a terrorist attack. As a result of the supplemented DBT, the security of spent fuel pools has been enhanced at operating power reactors. In addition, PRM–73–12 was filed by the Committee to Bridge the Gap on July 23, 2004, and was published for comment (69 FR 64690; November 8, 2004).
Part of this program includes conducting Comprehensive Reviews of commercial nuclear site security. Other commenters suggested that the NRC's rationale for limiting the characteristics of the DBTs to the attacks against which a private security force could reasonably be expected to defend appears to be based on cost considerations, which is not permitted for measures that are necessary for the protection of public safety. The Commission concludes that the amendments to § 73.1 will continue to ensure adequate protection of public health and safety and the common defense and security by requiring the secure use and management of radioactive materials. The revised DBTs represent the largest threats against which private sector facilities must be able to defend with high assurance.
Sufficient blackstart resources, located in specific locations within each interconnection, are the last line of defense against a prolonged blackout. In an earlier blog,[1] I discussed the need to create a Design Basis Threat (“DBT”) for blackstart in the face of new and emerging threats, and then conduct the necessary planning studies to ensure there is sufficient and operable blackstart generation available. In addition, there is a need to include flexible blackstart processes to restart the electric grid following interconnection-wide blackouts. The Design-Basis Threat (DBT) Report is a profile of the type, composition, capabilities, methods (tactics, techniques, and procedures), and the goals, intent, and motivation of an adversary upon which the security engineering and operations of a facility are based. A profile of the type, composition, capabilities, methods (tactics, techniques, and procedures), and the goals, intent, and motivation of an adversary upon which the security engineering and operations of a facility are based.


No comments:
Post a Comment